FTID fraud requires sophisticated hacking to produce manipulated shipping labels that can spoof the carriers’ delivery systems.
The StartOps Team
TLDR:
In this StartOps Guide, we unpack FTID fraud. What is it? Who's vulnerable? And what do you do if your brand becomes a target?
This Guide was produced in collaboration with Tailed. Tailed helps mid-market ecommerce companies detect and block fraudulent returns. Check out their page in the StartOps Directory.
What is FTID fraud?
FTID fraud is a technologically sophisticated form of refund fraud in which a fraudster alters a return shipping label for an ecommerce order to receive a refund, while still keeping the merchandise for which the refund was granted.
How widespread is FTID fraud?
Industry estimates suggest that FTID fraud may cost retailers up to $18 billion per year as of 2024, affecting tens of thousands of merchants.
FTID fraud requires sophisticated hacking to produce manipulated shipping labels that can spoof the carriers’ delivery systems. Only a limited number illegal hacking groups possess this capability.
However, FTID fraud has been able to grow quickly because hacking groups can offer 'fraud-as-a-service' to hundreds of thousands of non-technical consumers via messaging groups on Telegram and the dark web.
Once a vulnerable brand is discovered and announced in a chat, thousands of customers may descend to buy and return items before the vulnerability is caught and stopped.
The issue of FTID fraud has also been exacerbated by the existence of cashout groups. These fully-legal organizations buy popular goods at a low price, e.g. by taking advantage of sales and discount codes. Then they re-sell them for a markup on marketplaces like eBay and Amazon. Many of these groups will buy goods with no questions asked, making it easy for FTID fraudsters to liquidate their inventory.
How is the fraud perpetrated?
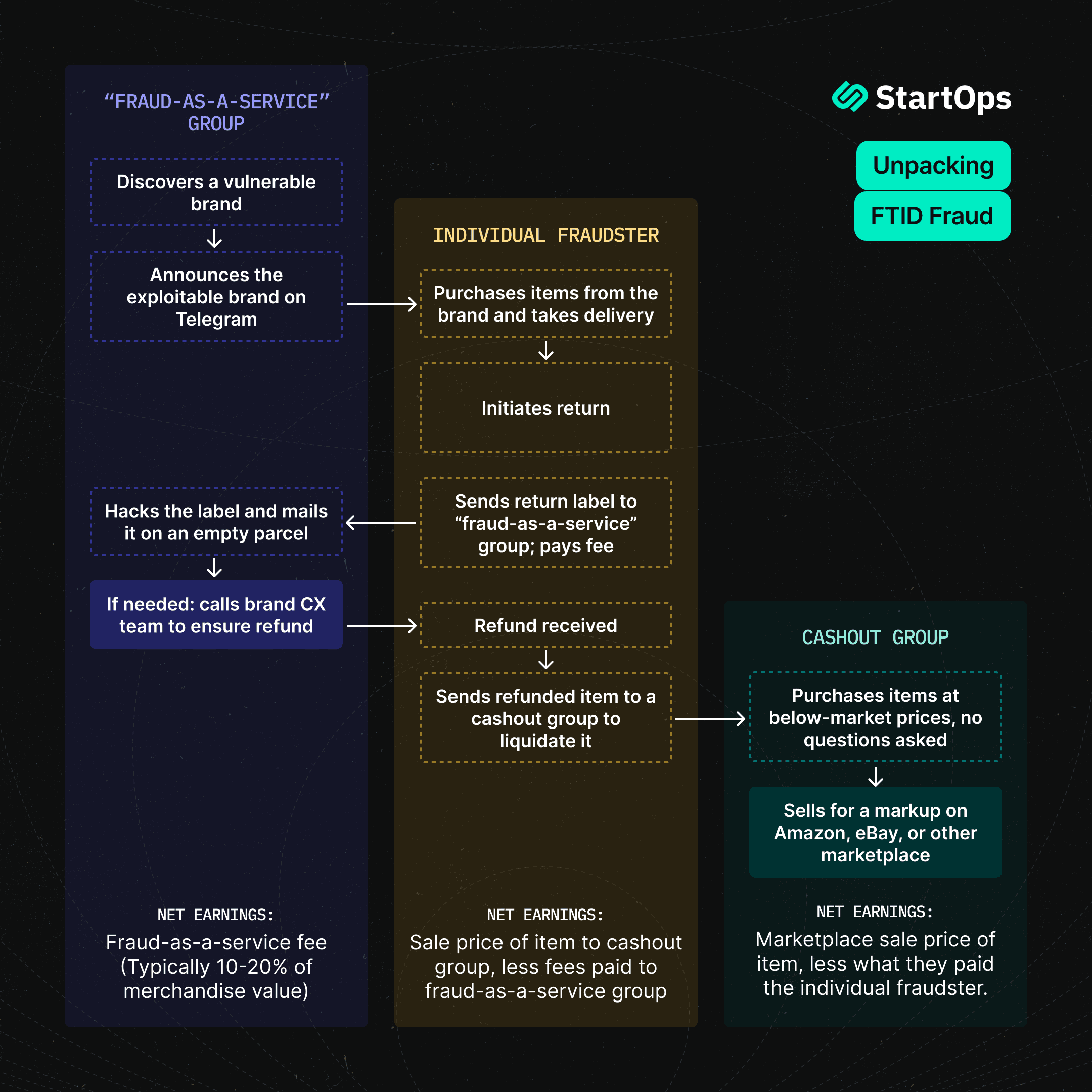
Here's how it works:
An individual fraudster learns about a new exploitable brand in a fraud-as-a-service message group.
They place an order for an item with the target brand.
When the item arrives, the fraudster requests a refund and generates a return label.
The fraudster then sends the return label to the fraud-as-a-service provider (along with a fee).
The fraud-as-a-service provider hacks the label on the fraudster's behalf. Specifically, they change the shipment's destination address on the return label to an address near —but not at — the original delivery address.
The hacked return label is placed on an empty parcel and shipped.
When the empty parcel is dropped off (at the incorrect address), it receives a “Delivered” tracking scan from the carrier.
This final tracking scan triggers the merchant’s returns platform to issue the refund to the customer.
[Optional] The fraudster sells their now-free item on to a cashout group.
The end result is that:
The brand has paid return postage and issued a refund for an item they never receive
The fraudster has kept the merchandise
The hacker has pocketed their fraud-as-a-service fee
A cashout group has fenced the merchandise
An unassuming third party has received an empty package
Who is vulnerable to FTID fraud?
Any retailer can be affected, but fraudsters prefer to target retailers that sell high-value products and automate return refunds. All carriers are vulnerable to this exploit, though some hacks are more effective than others on different carriers.
How do you know if you’re a victim of FTID fraud?
One-off instances of FTID fraud can be difficult to detect. Companies can experience much bigger economic impact when they become targets of fraud-as-a-service groups who make orders en masse. Signs that this might be happening include:
A spike in high-value returns not received by your warehouse.
Your warehouse receiving empty boxes or mailers. These are attempts at FTID Fraud where the carrier has corrected and replaced the return shipping label.
You see unauthorized shops selling your products on Amazon or eBay.
If this is happening to your brand, you should take corrective action as soon as you can.
Is there anything you can do about it?
Yes. Retailers who are experiencing FTID fraud generally have two options:
Option 1 — Change refund issuance methods
FTID fraud is easier to commit when refunds are issued before verifying physical receipt of returned items. (Certain forms of returns fraud can still be committed via social engineering, though it’s harder for fraudsters to do this at scale.)
Brands who are concerned about FTID fraud can ensure they are only issuing refunds upon physical receipt and inspection of the refunded order. This typically works best if:
The brand is operationally set up to keep return processing SLAs very tight (to minimize impact on the customer experience).
The return shipping costs for the item aren’t too high (since return shipping costs are still incurred regardless of whether the return is fraudulent).
Option 2 — Use an FTID fraud detection service.
FTID fraud detection software can identify potentially fraudulent orders before they’re refunded, using a variety of fingerprinting techniques.
If fraudulent purchases can be blocked even before the shipping label is generated, this has the added benefit of saving the brand on return postage. It can also quickly and clearly signal to fraudsters that the merchant is not a good target.
*****
Which approach is the most economical will depend on the merchant, their supply chain setup, and what they sell. Tools exist to help with both approaches:
Returns processing tools like Two Boxes can help brands achieve faster return inspections.
FTID fraud prevention services like Tailed can help block fraudulent orders from being refunded.
We hope this StartOps Guide has helped you learn about — and avoid — FTID fraud. If you have ideas for other Guides you'd like to see, we'd love to hear them! Drop us a note at support@startops.network.